Overview
Keysafe provides the most secure, private, and confidential Account Abstraction paradigm allowing users to access Web3 world by using their Web2 accounts.
Project details
The problem
Managing Web3 accounts could be cumbersome, unfriendly to users, and vulnerable to hacking. Based on research by ChainAnalysis, the number of lost bitcoins due to account loss reached 3.79 million($150 billion).
To use Web2 social login "OAuth" is user-friendly, but it is trust needed and is vulnerable to Web2 identity exposure.
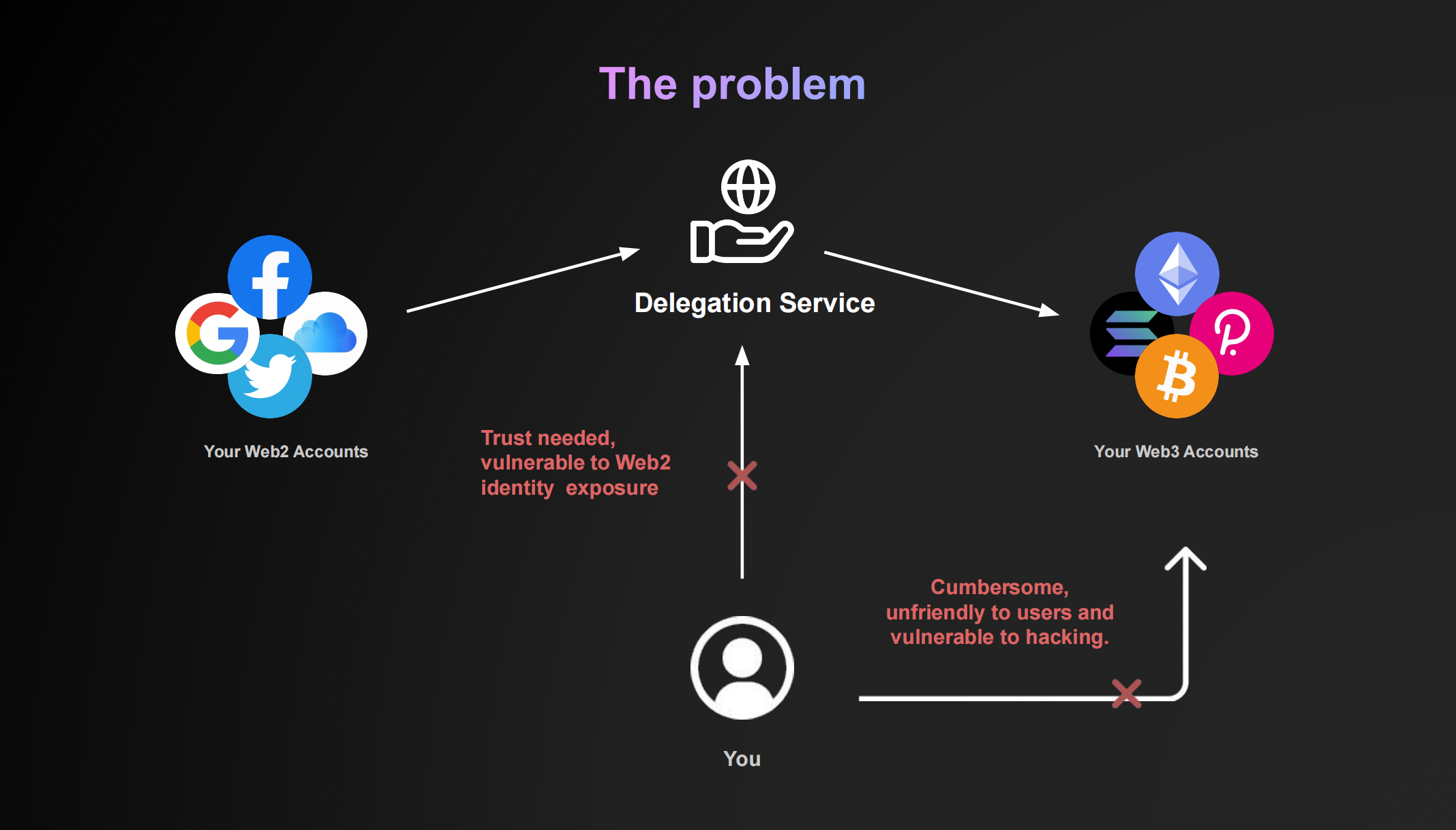
The key problem: account systems in web2 and web3 are natively separate, technically unconnected, and even inherently in conflict with their value.

The solution
Keysafe Protocol is the missing layer between Web2 and Web3 that connects users' Web2 and Web3 accounts in a decentralized, verifiable, and private way. With the connection, users can access their Web3 assets and Dapps through Web2 verification such as Google OAuth and Email verification.
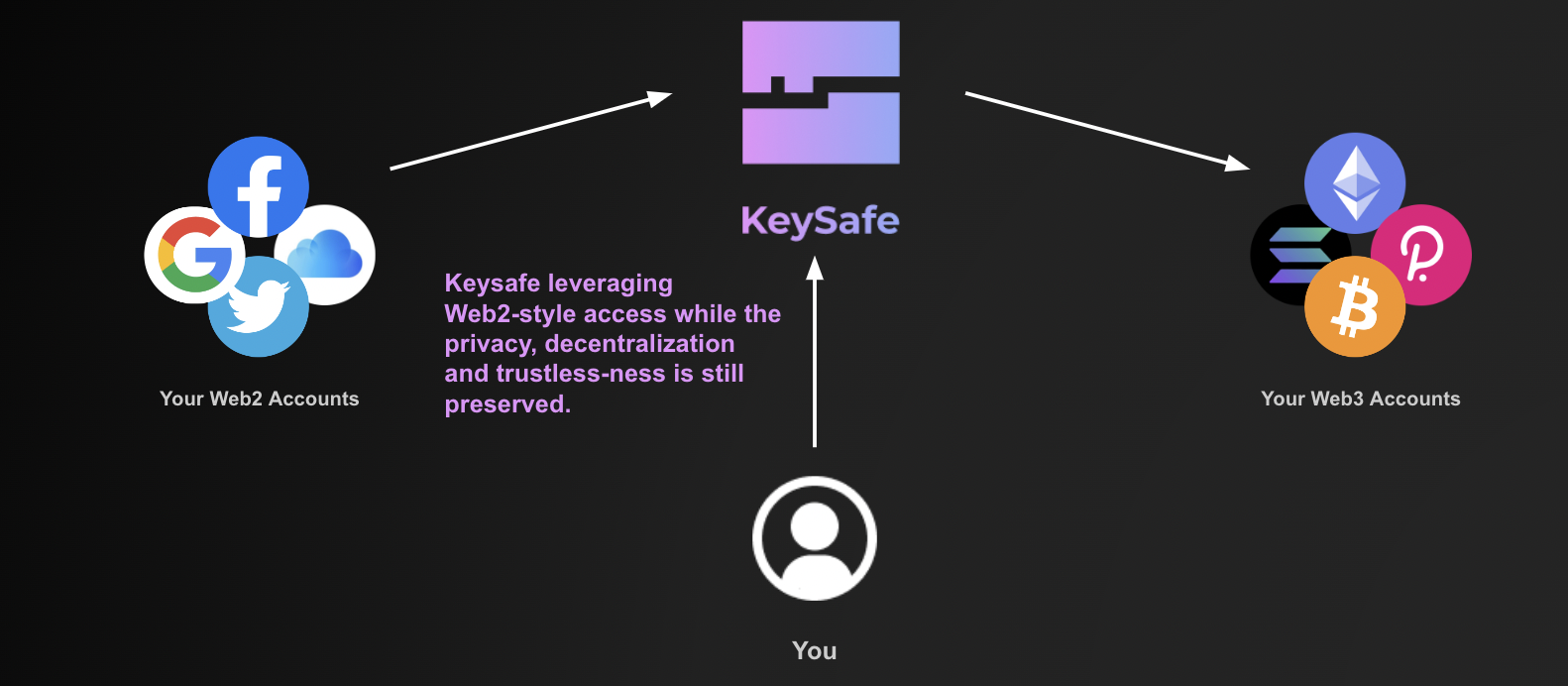
How we built it
keysafe consists of several modules both on-chain and off-chain.
Onchain modules:
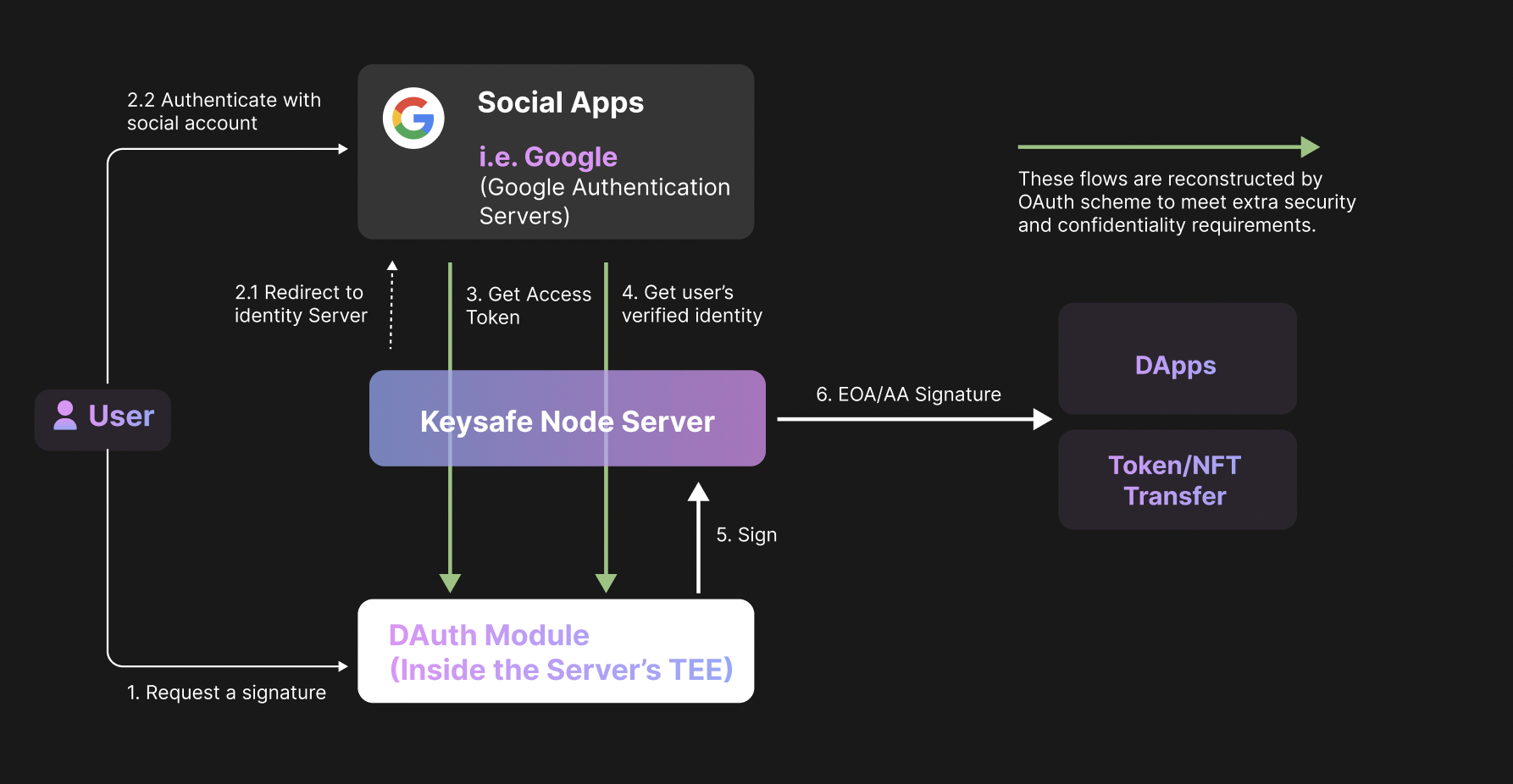
Contract: Keysafe deployed a smart contract on Aptos Network. The contract provides the registration function of the Keysafe node that allows users to verify the environment of the service node and the service result.
TEE's Public Key: Users could set up a private channel with Node's TEE by using TEE's public key that is registered on-chain.
The verifiable service result: The node's TEE environments and each service result can be verified on the contract. If the node has any misconduct, the contract will also deduct the node pledge accordingly.
Offchain modules:
TEE: Keysafe protocol uses Trusted Execution Environment (TEE) technology to manage user private keys.
MPC and BLS algorithms: Keysafe uses Secure Multi-party Computation (MPC) and Threshold BLS Signatures to decentralize and distribute user accounts to multiple nodes' TEE to get enhanced security.
DAuth: The most crucial and creative module of Kesyafe is DAuth. DAuth allows owners to access the Web3 world with a customized combination of Web2 third-party authentication services including SMS, email, Google, and even Web3 address.
Project challenges
97.5% of users are still waiting for Web3, we have to let more Web3 projects adopt and integrate Keysafe to form an ecosystem and hence gain a huge user base gradually;
To become a standard of Account Abstraction that remains decentralization, privacy and trustless;
Some usefule links
Vedio URL: Demo of Keysafe
Demo dApp: Demo dApp
Whitepaper: Keysafe Whitepaper
Project Test Instructions: How to user Kesyafe UI
Project Documents: Wiki
Github: Keysafe repos
Milestones
Keysafe core: Self custody of User accounts;
DAuth SDK: Web3.0 account recovery and transfer via users' Web2.0 authentications;
Kesyafe Wallet: EIP4337 compatibale that abstracts user's Web3.0 accounts into Web2.0 accounts, meanwhile, Unilogin could also let users to pay gas fee by using any alternative tokens;
2022-Q3: Build the Keysafe protocol prototype and deploy in Nile. [DONE]
2022-Q4: Build the Keysafe self-custody DApp [DOING]
2023-Q2: Build DAuth SDK. [DOING]
2023-Q4: Build Keysafe wallet.


